HR cloud systems store sensitive data. This data includes employee details, payroll, and more. A security audit checks if the data is secure. Let’s look at what is needed for HR cloud vendor security audits.
Why Are Security Audits Important?
Security audits are crucial. They check if your data is safe. They help find and fix security issues. Regular audits ensure ongoing protection. They also build trust with employees and clients.
Components of a Security Audit
A thorough security audit has many components. Let’s explore each one in detail.
1. Risk Assessment
The first step is a risk assessment. This identifies potential threats. It also finds areas where data is at risk. Risks can come from many sources. These include hackers, system failures, or even human error.
2. Access Control
Access control is about who can see and use the data. Only authorized people should have access. This limits the chances of a breach. Access control includes passwords, user roles, and permissions.
3. Data Encryption
Data encryption protects data. It converts data into code. Only authorized users can decode it. This keeps data safe even if it is intercepted.
4. Regular Updates And Patches
Systems need regular updates. Updates fix known security issues. Patches are small updates that address specific problems. Regular updates and patches are crucial for security.
5. Incident Response Plan
An incident response plan is a must. It outlines steps to take if there is a breach. This helps quickly contain and fix the issue. It also includes communication plans for informing affected parties.
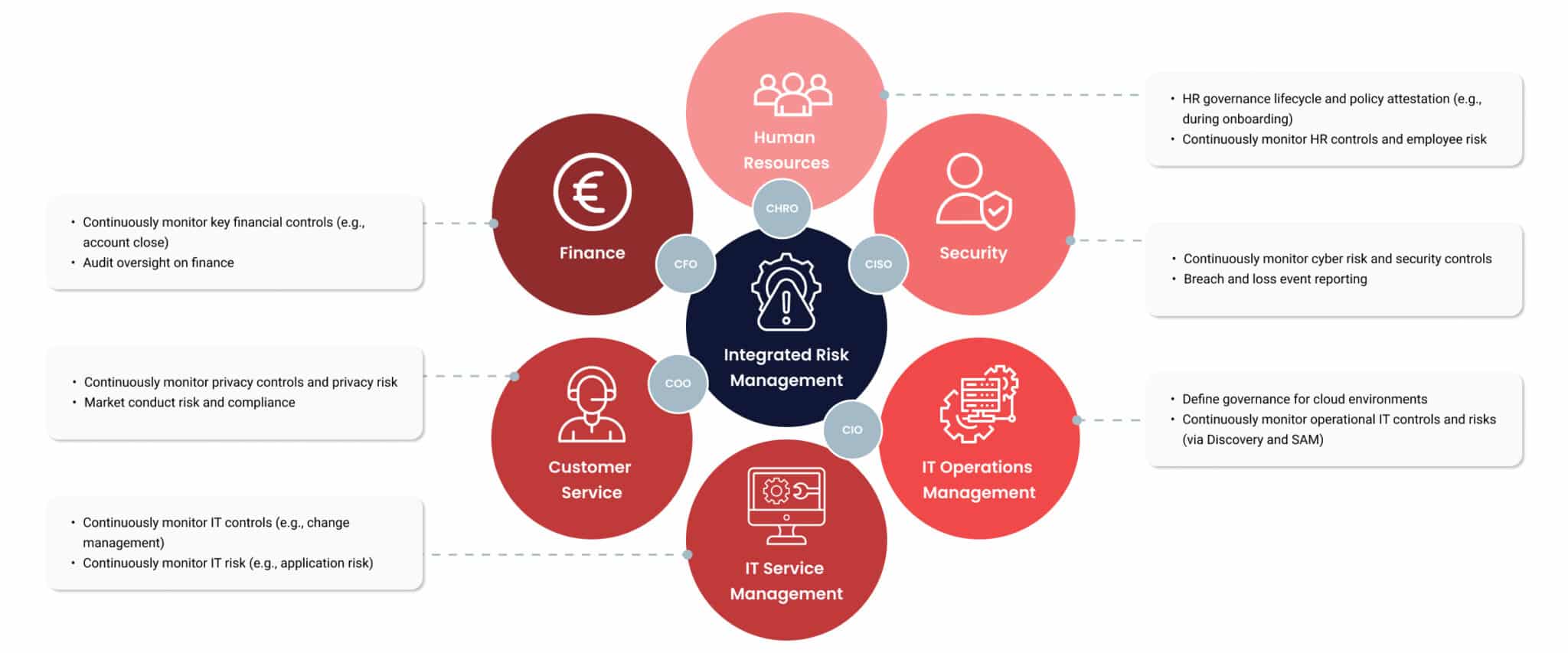
6. Vendor Management
HR cloud vendors must also be secure. Vendor management involves checking their security practices. This ensures they meet your security standards. Regular checks and audits of vendors are necessary.
7. Compliance
Compliance means following legal and regulatory requirements. Different industries have different rules. Make sure your HR cloud system meets these rules. Compliance helps avoid legal issues and penalties.
Steps to Conduct a Security Audit
Conducting a security audit involves several steps. Let’s break them down.
Step 1: Define The Scope
First, define the scope of the audit. Decide what systems and data will be reviewed. This helps focus the audit on critical areas.
Step 2: Gather Information
Next, gather information about the systems and data. This includes understanding how data is stored, accessed, and used. It also involves reviewing current security measures.
Step 3: Identify Risks
Identify potential risks to the data. Consider all possible sources of risk. This includes both internal and external threats.
Step 4: Review Access Controls
Review who has access to the data. Ensure that only authorized users can access sensitive information. Check that access controls are strong and effective.
Step 5: Test Security Measures
Test the current security measures. This includes testing encryption, firewalls, and other protections. Look for weaknesses that could be exploited.
Step 6: Review Incident Response Plan
Review the incident response plan. Ensure that it is up-to-date and effective. Test the plan to see if it works as expected.
Step 7: Check Compliance
Check that the system complies with relevant laws and regulations. Make sure all legal requirements are met.
Step 8: Report Findings
Finally, report the findings of the audit. This includes detailing any issues found. Provide recommendations for fixing these issues. A clear report helps take action to improve security.

Credit: northeast.newschannelnebraska.com
Best Practices for HR Cloud Security
Following best practices can help improve HR cloud security. Here are some tips:
- Use Strong Passwords: Ensure all users have strong passwords. Avoid common or easy-to-guess passwords.
- Enable Two-Factor Authentication: Add an extra layer of security. This requires a second form of identification.
- Regularly Update Systems: Keep all systems up-to-date with the latest patches and updates.
- Conduct Regular Training: Train employees on security best practices. Awareness helps prevent many security issues.
- Monitor Systems: Regularly monitor systems for unusual activity. Early detection helps prevent breaches.
Frequently Asked Questions
What Are Hr Cloud Vendor Security Audits?
HR Cloud Vendor Security Audits check the safety of cloud-based HR services.
Why Are Hr Cloud Vendor Security Audits Important?
They protect sensitive employee data from breaches and ensure compliance with regulations.
What Data Is Reviewed In Hr Cloud Vendor Security Audits?
Employee personal data, payroll information, and other sensitive records are reviewed.
How Often Should Hr Cloud Vendor Security Audits Be Conducted?
Audits should be done annually or after major system changes.
Conclusion
HR cloud vendor security audits are essential. They help protect sensitive data. Conducting thorough audits ensures data remains secure. Follow the steps and best practices outlined here. This will help maintain strong security for your HR cloud systems.