Biometric authentication is a way to confirm a person’s identity. In other words, they can locate each other based on their unique physical characteristics. Especially, this can include fingerprints, facial recognition, iris scans, and voice recognition.
Normally, a guy might use their fingerprint instead of a passcode to unlock their phone. To clarify, assume this scenario. The CEO of your organization is trying to gain entry into the secured office building. For instance, he might use his face scan, fingerprint, or iris scan to gain entry. In spite of, showing an ID card.
In these circumstances, biometric authentication begins as the first step of the identification. It starts with the person providing a sample of their biometric trait. Thus, to verify their identity, we take a fingerprint or scan of their face or iris.
Biometric authentication has better security than a password or ID card. Despite these challenges, biometrics remain practical. For instance, consider the privacy and security of stored data. By all means, the features might not be accessible to people with specific disabilities.
What is Biometric Authentication?
When someone logs in, biometric identification uses their unique bodily traits to make sure they are who they say they are. These traits, like fingerprints, face features, iris patterns, or even voice patterns, are hard to copy or fake, so they can be used to prove someone’s identity. In most biometric identification systems, a sample of the user’s biometric data is taken and stored safely and then compared to other examples when the user tries to log in. If the samples match, the person can get in. If they don’t, they can’t.
Here are some of the key points from the article:
- Biometric authentication uses unique physical characteristics to identify a person.
- Biometric authentication is more secure than passwords or PINs.
- Biometric authentication is faster and more convenient than passwords or PINs.
- Biometric authentication can be expensive.
- There are privacy concerns associated with biometric authentication.
How Does the Biometric Authentication Work?

This authentication system captures a biological data sample from a user. Then they compare the data to a stored model to verify the user’s identity. Following are the steps to complete the procedure:
Step 1:
To start the process, the user presents their biometric characteristics to the identification device. In brief, there are three types of scanners. i.e., facial scanners, fingerprint scanners, and microphones.
Step 2:
Second, the process captures the biometric sample. Then, converts its data into a digital template. This template represents a biometric characteristic mathematically.
Step 3:
Next, the software compares the captured template to the stored template. Thereafter, the platform verifies the user’s identity and grants access if the templates match. On the contrary, if the templates do not match, the algorithm denies access. The user may need to try again or use an alternative authentication method.
Methods of Biometric Authentication:
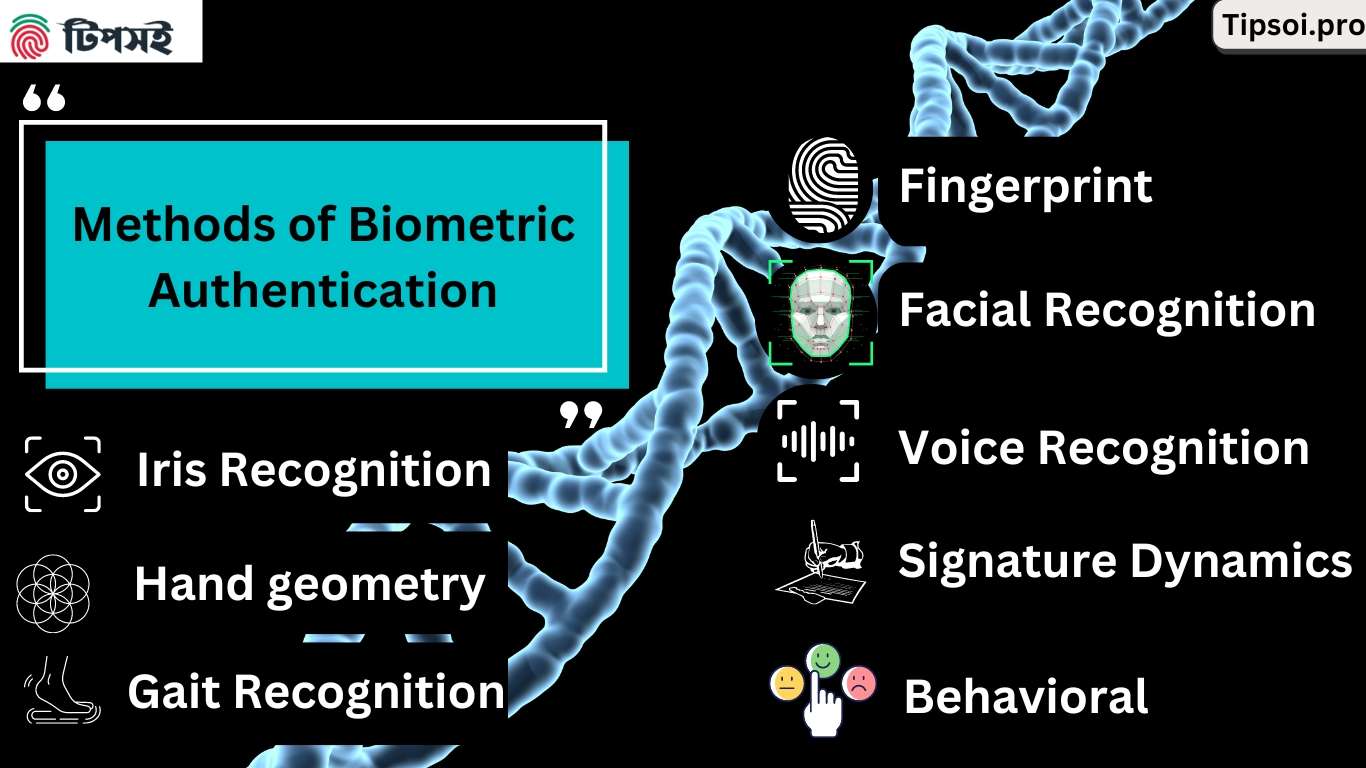
Fingerprint Authentication:
This method involves scanning a person’s fingerprint to confirm their identity. This time, A camera captures an image of the fingerprint. That is, to compare the image to a before-stored version to see if they match.
Facial Recognition:
This method uses a camera to capture a picture of someone’s face. Afterward, the system compares it to the stored data of that person’s face.
Iris Recognition:
This method uses a camera to capture an image of a person’s iris. Specifically, it captures the colored part of the eye. So that, the unique patterns in the iris confirm a person’s identity.
Voice Recognition:
This method involves capturing a sample of a person’s voice and comparing the sample to a before-recorded version to confirm their identity.
Hand geometry:
This method captures the size and shape of a person’s hand to confirm their identity. Based on the measurement of the lengths of the fingers, the hand’s breadth, and the hand’s shape.
Signature Dynamics:
This method captures a person’s signature to confirm their identity. Using a signature analysis program, it is possible to find how a person writes their signature. Such as their speed, pressure, and the angle of the pen on the paper.
Gait Recognition:
It’s possible to capture someone’s walk with a camera. Use this method to determine how they walk. Analyzes factors such as how they move and their stride length to confirm their identity.
Behavioral biometrics:
This method captures a person’s typing/mouse movement pattern to confirm their identity. Based on the way a person moves or interacts with their devices.
Advantages and Disadvantages of Biometric Authentication
Biometric authentication has revolutionized security systems, but it comes with both benefits and limitations. Here’s a breakdown:
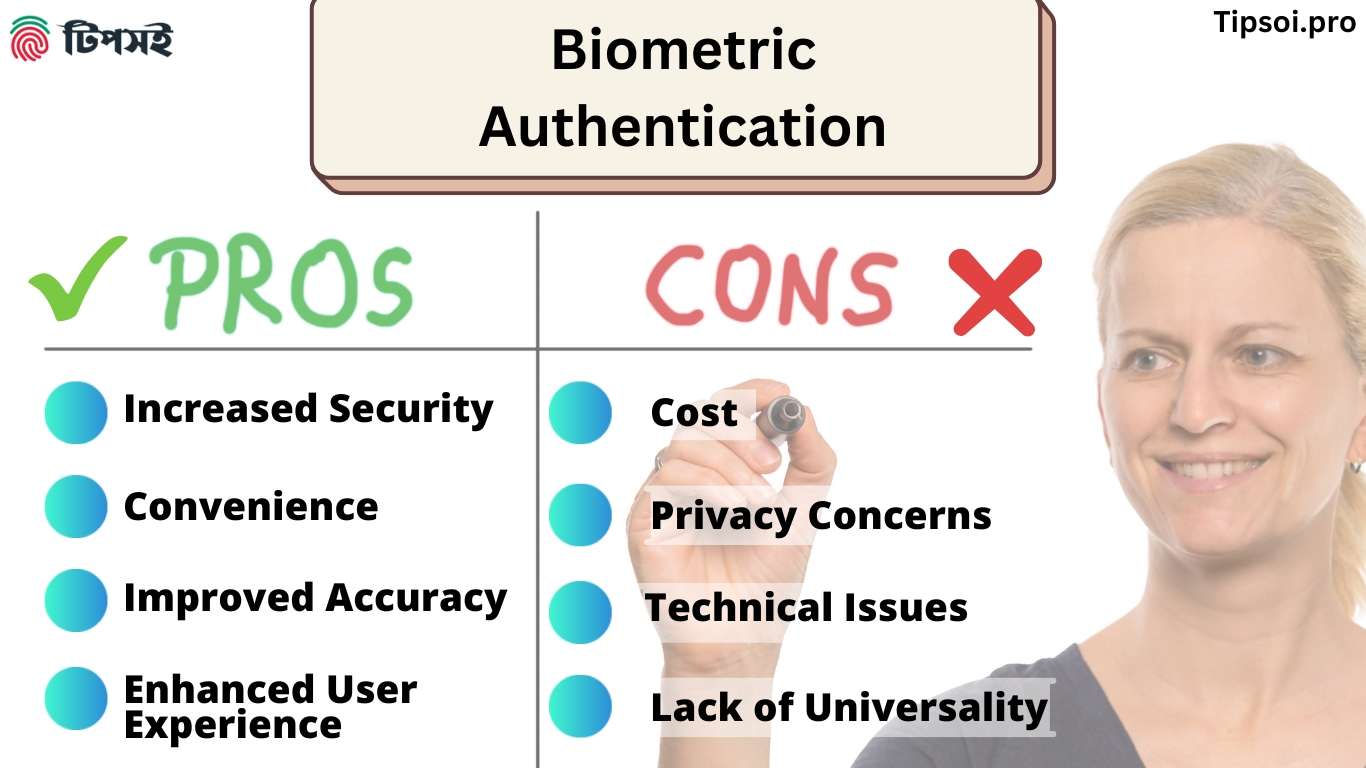
Benefits of Biometric Authentication
Here are some advantages of biometric authentication:
1. Increased Security:
Plenty of biometric methods are available today. Such as fingerprint scanning or facial recognition. Traditional methods aren’t as secure as these. Such as passwords or PINs. Because they are unique to the individual, and no one can replicate or steal them.
2. Convenience:
Biometric methods can be faster and more convenient for users. They do not need to remember passwords or carry physical tokens such as keycards or tokens.
3. Improved Accuracy:
Biometric methods can be more correct than traditional methods. They rely on unique physical characteristics that no one can forge or copy. Also, it helps with payroll management accuracy.
4. Enhanced User Experience:
This authentication can improve the user experience by providing a seamless and hassle-free login procedure.
What are the Biometric Authentication Challenges?
Here are some disadvantages or challenges of biometric authentication:
1. Cost:
This type of system can be quite expensive to start and keep. We need specialized hardware and software to capture and verify biometric data.
2. Privacy Concerns:
This might concern the people about the privacy implications of securing authentication with biometrics. As a whole, it involves the collection and storage of personal information. As an example, we can use fingerprints or facial images to find a person.
3. Technical Issues:
It’s possible to compromise biometric authentication methods. To technical issues such as false negatives. (Rejecting a valid user) or false positives (accepting an invalid user).
4. Lack of Universality:
This authentication method may only be suitable for this. Because of their physical characteristics, the people may not meet these requirements. (Such as fingerprints) or may have disabilities. That prevents them from using specific methods.
Biometric Authentication Use Cases
Case 1: Mobile Phone Unlocking
One everyday use case for this process is unlocking a mobile phone. Many smartphones now come with fingerprint scanners or facial recognition software. That allows users to unlock their phones by touching their fingers to the scanner and looking at the camera. Using this method protects your phone’s personal information reliably, efficiently, and confidentially.
Case 2: Banking and Financial Transactions
Financial institutions use this verification method to protect sensitive information. For example, a bank may use a facial recognition system or a fingerprint scanner. That is to verify the identity of customers while accessing their accounts or making transactions online or at ATMs. Banking and Financial Transactions can prevent fraudulent activity. And give customers a layer of security.
Case 3: Physical Access Control
The most common way to control access to physical spaces is with biometric authentication. Buildings or secure areas within a facility are some examples. Companies use fingerprint scanners and facial recognition software to let employees and visitors in. Physical Access Control can help to prevent unauthorized access. And improve security within the facility.
Case 4: Government and Military Applications
The government and military use biometric security to protect sensitive data. For example, military bases may use facial recognition or fingerprint scanners. The purpose of this process is to grant access to personnel and restricted areas. Government agencies may use biometric identification to verify the identity of employees. Contractors can also access sensitive data.
Conclusion
The last time biometrics were used to verify identities was centuries ago. The first recorded use of biometric identification was in ancient Babylon, where they used fingerprints to sign documents and seal business transactions.
Biometrics played an influential role in security during the 20th century. Cops used fingerprints to identify criminals and match them to crimes in the 1970s. To control access to secure facilities, they developed the first biometric security systems in the 1980s.
In the 1990s, technological advances developed into more sophisticated biometric authentication methods, such as iris scanning and facial recognition. People use these methods in high-security environments. Such as government agencies and military bases. Still, they became more adopted in commercial and consumer applications.
In the 21st century, biometrics have become prevalent. Smartphones and other devices now feature fingerprint scanners—and facial recognition software to unlock screens and protect access to personal data. There are also a lot of industries that use it. Including banking, healthcare, and transportation, to improve security and convenience for users.
Technology for biometric security is evolving. People will develop this in broader applications. The experts predict that this way of authentication will replace traditional methods. Such as passwords and PINs, as the primary means of verifying identity.
Related Posts:
The Importance of Payroll Management System in Bangladesh
Payroll Software Price in Bangladesh: Compare Top 5
Biometric Authentication Devices by Tipsoi:
FAQs
What are the advantages of biometric authentication?
Biometric authentication offers enhanced security, convenience, and improved user experience. It eliminates the need for passwords and provides non-transferable access, making it resistant to fraud and phishing attempts.
What are the disadvantages of biometric authentication?
Disadvantages include high implementation costs, privacy concerns, and technical issues such as failed authentication in edge cases. Additionally, biometric data cannot be reset if compromised.
How does biometric authentication work?
Biometric authentication works by capturing a person’s unique physical or behavioral traits (e.g., fingerprints or facial features) through sensors. These traits are stored as templates and compared during authentication to verify identity.
Is biometric authentication better than traditional methods like passwords?
Yes, biometric authentication is more secure and convenient than traditional methods like passwords or PINs. It eliminates risks associated with forgotten passwords and reduces vulnerability to hacking attempts.
Can biometric data be stolen or misused?
While biometric data is harder to steal than passwords, it is not immune to breaches. Storing biometric data locally instead of on centralized servers can reduce risks of misuse.
What are the risks associated with biometric authentication?
Risks include data breaches, privacy concerns, inaccuracies due to biased training data, and system failures in certain conditions (e.g., wet fingerprints or sore throats affecting voice recognition).