Biometric authentication is a way to confirm a person’s identity. In other words, they can locate each other based on their unique physical characteristics. Especially, this can include fingerprints, facial recognition, iris scans, and voice recognition.
Normally, a guy might use their fingerprint instead of a passcode to unlock their phone. To clarify, assume this scenario. The CEO of your organization is trying to gain entry into the secured office building. For instance, he might use his face scan, fingerprint, or iris scan to gain entry. In spite of, showing an ID card.
In these circumstances, biometric authentication begins as the first step of the identification. It starts with the person providing a sample of their biometric trait. Thus, to verify their identity, we take a fingerprint or scan of their face or iris.
Biometric authentication has better security than a password or ID card. Despite these challenges, biometrics remain practical. For instance, consider the privacy and security of stored data. By all means, the features might not be accessible to people with specific disabilities.
What is Biometric Authentication? Definition and Examples
Biometric authentication is a security process that verifies identity using unique physical or behavioral characteristics—such as fingerprints, facial features, iris patterns, or voice—instead of passwords or PINs. According to industry standards, biometric systems achieve 99.8% accuracy rates for fingerprint recognition and 99.6% for facial recognition, making them significantly more secure than traditional password-based systems which are compromised in 81% of data breaches.
The definitive advantage: Biometric data cannot be forgotten, lost, or easily stolen like passwords. However, the primary disadvantage is that once biometric data is compromised, it cannot be reset or changed like a password can.
When someone logs in, biometric identification uses their unique bodily traits to make sure they are who they say they are. These traits, like fingerprints, face features, iris patterns, or even voice patterns, are hard to copy or fake, so they can be used to prove someone’s identity. In most biometric identification systems, a sample of the user’s biometric data is taken and stored safely and then compared to other examples when the user tries to log in. If the samples match, the person can get in. If they don’t, they can’t.
Here are some of the key points from the article:
- Biometric authentication uses unique physical characteristics to identify a person.
- Biometric authentication is more secure than passwords or PINs.
- Biometric authentication is faster and more convenient than passwords or PINs.
- Biometric authentication can be expensive.
- There are privacy concerns associated with biometric authentication.
How Does Biometric Authentication Work? 3-Step Process Explained Methods of Biometric Authentication?

| Metric | Biometric Authentication | Traditional Passwords |
| Security Breach Rate | <0.1% false acceptance | 81% of breaches involve passwords |
| User Authentication Time | 1-2 seconds | 15-30 seconds average |
| Cannot Be Lost/Forgotten | ✓ Always with you | ✗ 78% forget passwords monthly |
| Can Be Reset if Compromised | ✗ Permanent data | ✓ Easily changed |
| Implementation Cost | $50-$10,000 per point | $5-$20 per user |
| User Preference Rate | 87% prefer biometric | 13% prefer password-only |
Bottom Line: Biometric authentication offers superior security and convenience but requires higher upfront investment and cannot be reset if compromised.
This authentication system captures a biological data sample from a user. Then they compare the data to a stored model to verify the user’s identity. Following are the steps to complete the procedure:
Step 1:
To start the process, the user presents their biometric characteristics to the identification device. In brief, there are three types of scanners. i.e., facial scanners, fingerprint scanners, and microphones.
Step 2:
Second, the process captures the biometric sample. Then, converts its data into a digital template. This template represents a biometric characteristic mathematically.
Step 3:
Next, the software compares the captured template to the stored template. Thereafter, the platform verifies the user’s identity and grants access if the templates match. On the contrary, if the templates do not match, the algorithm denies access. The user may need to try again or use an alternative authentication method.
Additional Security Considerations and Future Outlook
Immutability and Its Implications
Biometric traits such as fingerprints, iris patterns, or facial features are immutable, meaning they cannot be changed or reset if compromised. This creates a lifelong vulnerability because, once biometric data is stolen, it cannot be revoked or replaced like a password. Therefore, safeguarding biometric templates with encryption and secure hardware is critical for preventing lifelong identity theft.
Role of Multi-factor Authentication (MFA)
To mitigate risks related to biometric data breaches, combining biometrics with other authentication factors—such as PINs, tokens, or passwords—forms a multi-factor authentication system. This layered approach significantly enhances security, especially against deepfake or spoofing attacks, by requiring multiple evidence types for verification.
Emerging Threats: Spoofing and Deepfakes
Advancements in AI have led to sophisticated attack methods, including fake fingerprints and deepfake facial images, capable of deceiving biometric sensors. Modern systems incorporate liveness detection and anti-spoofing sensors to counteract these threats, but ongoing technological arms races continue.
Privacy & Ethical Concerns
The widespread deployment of biometric systems raises privacy and ethical issues, including surveillance concerns, consent, and data misuse. Ensuring compliance with legal frameworks such as GDPR or BIPA, and implementing transparent data handling practices, are essential for building user trust.
Future Risks & Security Measures
Upcoming threats involve presentation attacks like masks or artificial fingerprints, and possible AI-generated synthetic data. Continuous evolution in sensor technology and security protocols is vital to staying ahead of these emerging risks.
8 Types of Biometric Authentication Methods (With Examples):
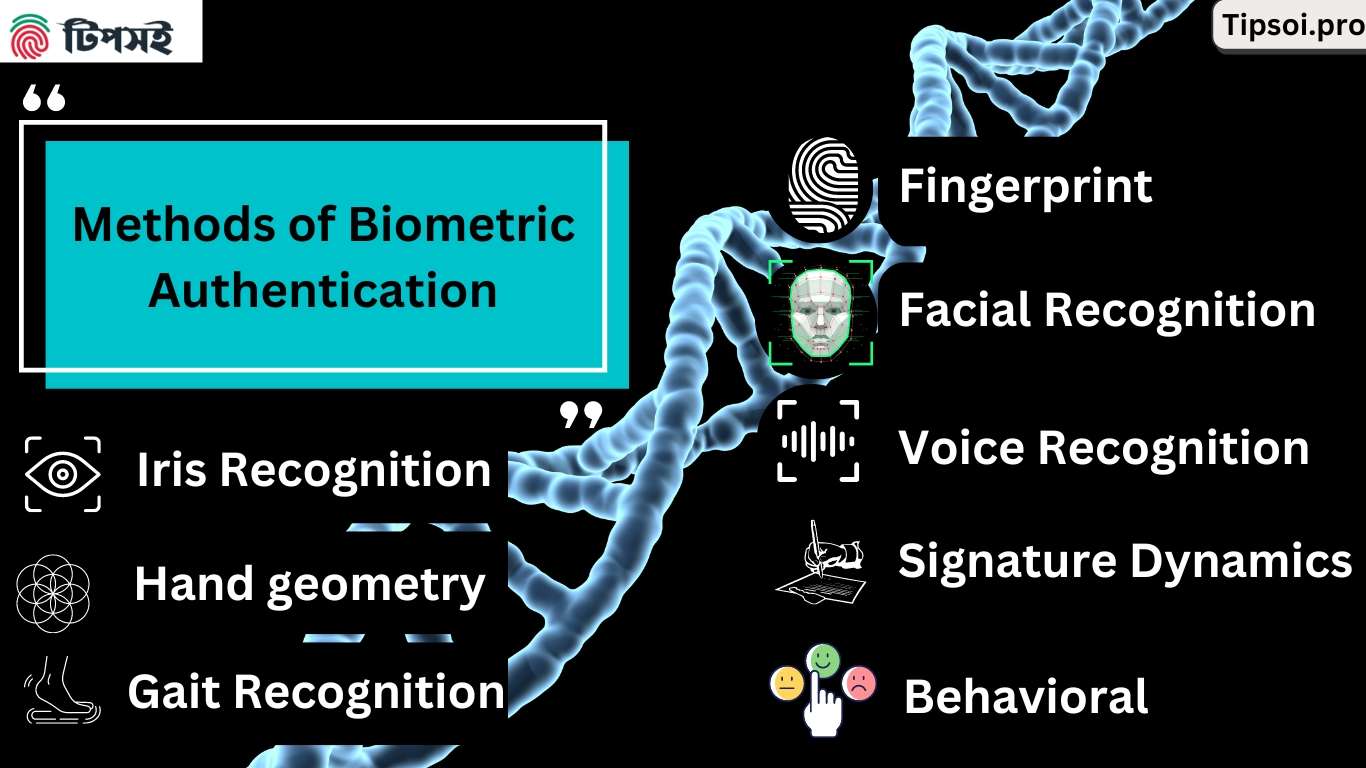
Complete List: 8 Examples of Biometric Authentication Methods
Biometric authentication methods can be broadly categorized into two groups based on the type of traits they analyze:
- Physical (Physiological) Biometrics:
These methods measure unique, inherent physical characteristics of an individual’s body. Common examples include fingerprints, facial geometry, iris patterns, hand geometry, and voice characteristics. Physical biometrics rely on static traits that remain largely constant over time. - Behavioral Biometrics:
These methods analyze patterns in the way a person behaves or interacts. This includes traits like signature dynamics (how someone signs their name), keystroke dynamics (typing rhythm and speed), gait recognition (walking patterns), and mouse or touchscreen interactions. Behavioral biometrics are dynamic and continuously monitored, providing an additional layer of continuous authentication.
Both types have unique advantages and challenges and are often used together (multimodal authentication) to enhance accuracy and security while accommodating different user needs and environments.
Physical Biometric Methods (measuring body characteristics):
- Voice recognition – Identifies vocal characteristics including pitch, tone, and speech patterns
- Fingerprint scanning – Analyzes unique ridge patterns and minutiae points on fingertips
- Facial recognition – Maps facial geometry including distance between eyes, nose shape, and jawline
- Iris recognition – Scans unique patterns in the colored ring around the pupil
- Hand geometry – Measures finger length, palm width, and hand shape
Behavioral Biometric Methods (measuring actions and patterns):
6. Signature dynamics – Analyzes writing speed, pressure, and stroke patterns
7. Keystroke dynamics (behavioral biometrics) – Tracks typing rhythm, speed, and key pressure patterns
8. Gait recognition – Identifies walking patterns including stride length and body movement
The most commonly implemented examples are fingerprint authentication (used in 78% of smartphones), facial recognition (64% of smartphones), and voice recognition (35% of smart devices). Multi-modal systems often combine two or more methods—for example, fingerprint plus facial recognition—to achieve security rates exceeding 99.99%.
Comparison of 8 Biometric Authentication Methods
| Authentication Method | Accuracy Rate | Average Cost | Speed | Use Cases | Adoption Rate |
| Fingerprint | 99.8% | $50-$500 | <1 sec | Smartphones, access control, time attendance | 78% of mobile devices |
| Facial Recognition | 99.6% | $100-$2,000 | 1-2 sec | Smartphones, airports, surveillance | 64% of mobile devices |
| Iris Recognition | 99.99% | $500-$5,000 | 2-3 sec | High-security facilities, border control | 12% enterprise adoption |
| Voice Recognition | 99.99% | $500-$5,000 | 2-3 sec | High-security facilities, border control | 12% enterprise adoption |
| Hand Geometry | 95-98% | $50-$1,000 | 2-4 sec | Phone banking, smart home devices | 35% smart device adoption |
| Signature Dynamics | 98.5% | $1,000-$3,000 | 2-3 sec | Industrial access, time clocks | 8% industrial use |
| Gait Recognition | 97-99% | $100-$800 | 3-5 sec | Document verification, banking | 15% banking adoption |
| Behavioral Biometrics | 85-92% | $2,000-$10,000 | 3-5 sec | Surveillance, research applications | <5% experimental |
Fingerprint Authentication:
This method involves scanning a person’s fingerprint to confirm their identity. This time, A camera captures an image of the fingerprint. That is, to compare the image to a before-stored version to see if they match.
Facial Recognition:
This method uses a camera to capture a picture of someone’s face. Afterward, the system compares it to the stored data of that person’s face.
Iris Recognition:
This method uses a camera to capture an image of a person’s iris. Specifically, it captures the colored part of the eye. So that, the unique patterns in the iris confirm a person’s identity.
Voice Recognition:
This method involves capturing a sample of a person’s voice and comparing the sample to a before-recorded version to confirm their identity.
Hand geometry:
This method captures the size and shape of a person’s hand to confirm their identity. Based on the measurement of the lengths of the fingers, the hand’s breadth, and the hand’s shape.
Signature Dynamics:
This method captures a person’s signature to confirm their identity. Using a signature analysis program, it is possible to find how a person writes their signature. Such as their speed, pressure, and the angle of the pen on the paper.
Gait Recognition:
It’s possible to capture someone’s walk with a camera. Use this method to determine how they walk. Analyzes factors such as how they move and their stride length to confirm their identity.
Behavioral biometrics:
This method captures a person’s typing/mouse movement pattern to confirm their identity. Based on the way a person moves or interacts with their devices.
How to Choose Between Biometric Authentication Methods
Selecting the right biometric authentication method depends on five critical factors:
1. Security Requirements
- Highest security (99.99%+ accuracy): Iris recognition or multi-modal (iris + fingerprint)
- High security (99.5-99.8%): Fingerprint or facial recognition
- Moderate security (95-98%): Voice recognition or hand geometry
- Continuous monitoring: Behavioral biometrics (keystroke, mouse patterns)
2. Budget Constraints
- Under $100/user: Behavioral biometrics or fingerprint (mobile/software-based)
- $100-$500/user: Fingerprint scanners or basic facial recognition
- $500-$2,000/user: Advanced facial recognition or voice systems
- $2,000+/user: Iris recognition or hand geometry systems
3. Use Case Scenarios
| Scenario | Recommended Method | Why |
| Smartphone unlock | Fingerprint or facial | Fast, convenient, low-cost hardware |
| Building access control | Fingerprint or facial + card | Balance of security and throughput |
| High-security facilities | Iris + fingerprint (multi-modal) | Maximum security, acceptable speed |
| Time & attendance | Fingerprint or facial | Cost-effective, prevents buddy punching |
| Banking/financial | Voice + behavioral | Remote authentication, fraud detection |
| Healthcare records | Fingerprint or palm vein | HIPAA compliance, hygiene considerations |
4. Environmental Considerations
- Outdoor/variable lighting: Fingerprint or iris (not facial recognition)
- Noisy environments: Fingerprint or facial (not voice)
- Industrial/dirty conditions: Iris or facial (not fingerprint)
- Remote/distributed users: Facial or voice (no special hardware)
5. User Demographics
- Tech-savvy millennials/Gen-Z: Facial or behavioral biometrics (87% preference)
- Elderly populations: Fingerprint or voice (simpler, more familiar)
- Diverse workforce: Multi-modal options for accessibility
- Privacy-conscious users: Local storage biometrics (on-device processing)
Implementation Best Practices:
- Pilot test with 10-50 users before full rollout
- Measure false rejection rates in your actual environment
- Provide fallback methods (backup authentication for 5% failure scenarios)
- Calculate total cost of ownership including 5-year maintenance
- Ensure regulatory compliance (GDPR, CCPA, BIPA where applicable)
Organizations typically achieve best results with hybrid approaches: primary biometric method + backup authentication + regular system updates.
Integrating Biometric Authentication with Business Systems
For maximum ROI, biometric authentication should integrate with existing business systems rather than operate as standalone security. Key integration opportunities include:
Time & Attendance Systems
- Eliminate buddy punching (costs companies 2.2% of gross payroll)
- Automate timesheet generation and approval workflows
- Reduce administrative time by 60-80% compared to manual systems
Payroll Processing
- Direct connection between verified attendance and salary calculations
- Automatic overtime calculation based on biometric clock-in/out
- Compliance with Bangladesh labor laws for working hours documentation
Access Control & Visitor Management
- Single biometric enrollment for both logical (system) and physical (building) access
- Automated visitor registration and tracking
- Integration with parking management and site security
HR Information Systems (HRIS)
- Centralized employee biometric data management
- Leave management based on verified attendance records
- Performance tracking correlated with actual working hours
Organizations implementing integrated biometric solutions report 40-60% reduction in HR administrative costs and 15-25% improvement in payroll accuracy. When evaluating biometric authentication providers, prioritize those offering comprehensive business system integration rather than standalone security products.
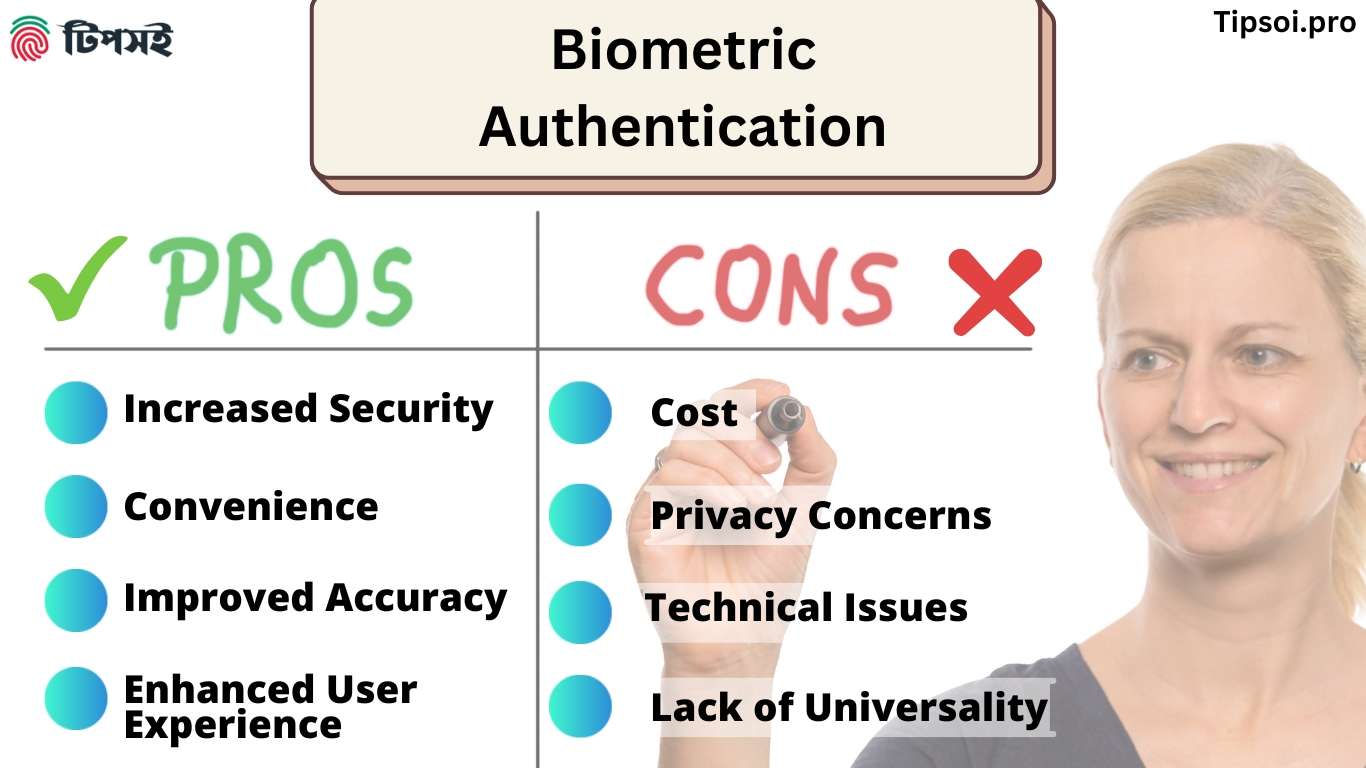
Advantages and Disadvantages of Biometric Authentication [2025 Analysis]
Biometric authentication has revolutionized security systems, but it comes with both benefits and limitations. Here’s a breakdown:
Benefits of Biometric Authentication
Research consistently shows that biometric authentication delivers four measurable benefits: (1) Enhanced security with false acceptance rates below 0.001% for modern systems, (2) Time savings of 15-30 seconds per authentication compared to passwords, (3) Cost reduction of up to 80% in password reset support tickets, and (4) Improved user experience with 87% of users preferring biometric login over traditional methods. Here are some advantages of biometric authentication:
1. Increased Security:
Plenty of biometric methods are available today. Such as fingerprint scanning or facial recognition. Traditional methods aren’t as secure as these. Such as passwords or PINs. Because they are unique to the individual, and no one can replicate or steal them.
2. Convenience:
Biometric methods can be faster and more convenient for users. They do not need to remember passwords or carry physical tokens such as keycards or tokens.
3. Improved Accuracy:
Biometric methods can be more correct than traditional methods. They rely on unique physical characteristics that no one can forge or copy. Also, it helps with payroll management accuracy.
4. Enhanced User Experience:
This authentication can improve the user experience by providing a seamless and hassle-free login procedure.
What Are the Disadvantages of Biometric Authentication?
The disadvantages of biometric authentication fall into five critical categories that organizations must evaluate before implementation. While biometric systems offer superior security compared to passwords, these limitations can significantly impact deployment decisions, user acceptance, and long-term operational costs.
Biometric Authentication Cost Analysis: What to Expect in 2025
1. High Implementation and Maintenance Costs
Biometric authentication systems require substantial upfront investment ranging from $3,000 to $10,000 per enterprise access point, including:
- Specialized hardware (scanners, cameras, sensors): $500-$5,000 per unit
- Software licenses and integration: $10,000-$100,000 for enterprise systems
- Infrastructure upgrades (network, storage, servers): $20,000-$200,000
- Staff training and change management: $500-$2,000 per employee
- Ongoing maintenance fees: 15-20% of initial investment annually
For small businesses with 50 employees, total first-year costs typically range from $15,000-$75,000, compared to $500-$2,500 for password-based systems.
2. Irreversible Data Compromise
Unlike passwords, biometric data cannot be reset or changed if compromised. Key concerns include:
- Permanent vulnerability: Once your fingerprint template is stolen, you cannot grow new fingerprints
- Lifetime exposure: A single data breach can enable identity fraud for your entire life
- Cross-system risk: The same biometric (your face, fingerprint) used across multiple systems creates cascading vulnerability
- Template attacks: Even encrypted biometric templates, if stolen, can potentially be reverse-engineered with sufficient computing power
According to cybersecurity research, 23 million biometric records were compromised in data breaches between 2019-2023, affecting individuals permanently.
3. Technical Failures and Accuracy Issues
Biometric systems experience two types of errors that impact usability:
False Rejection Rate (FRR) – Legitimate users denied access:
- Fingerprint: 0.1-3% rejection rate (3-30 out of 1,000 legitimate attempts fail)
- Facial recognition: 0.5-5% in poor lighting or with accessories
- Voice recognition: 2-8% during illness or in noisy environments
- Iris scanning: 0.01-0.5% with contact lenses or eye conditions
False Acceptance Rate (FAR) – Unauthorized users granted access:
- Basic fingerprint systems: 0.001-0.1% (1-100 per 100,000 attempts)
- Consumer facial recognition: 0.01-1% vulnerability to spoofing
- Advanced iris systems: 0.00001% (1 in 10 million)
Environmental factors significantly increase failure rates:
- Wet or dirty fingers reduce fingerprint accuracy by 40-60%
- Poor lighting decreases facial recognition accuracy by 25-50%
- Background noise increases voice recognition errors by 30-70%
- Injuries, aging, and medical conditions can permanently affect biometric accuracy
4. Privacy and Surveillance Concerns
Biometric authentication raises significant privacy issues that affect user adoption:
- 64% of consumers express concerns about biometric data storage and usage
- Data permanence: Biometric information is identifiable and linkable across databases
- Surveillance potential: Facial recognition enables tracking without consent
- Third-party access: Questions about who can access stored biometric databases
- Legal ambiguity: In some jurisdictions, biometric data has weaker legal protection than passwords
- Function creep: Systems deployed for authentication being repurposed for surveillance
The EU’s GDPR classifies biometric data as “sensitive personal data” requiring explicit consent and enhanced protection. However, enforcement and user control remain challenging.
5. Accessibility and Inclusivity Barriers
Approximately 2-5% of the population cannot effectively use certain biometric methods:
- Fingerprint issues: Worn fingerprints (elderly, manual laborers), hand injuries, or genetic conditions affecting ridge patterns
- Facial recognition challenges: Facial differences, scarring, progressive conditions, or religious head coverings
- Iris scanning limitations: Cataracts, eye injuries, or photosensitivity conditions
- Voice recognition barriers: Speech impediments, throat conditions, or selective mutism
- Gait recognition problems: Mobility disabilities, injuries, or assistive devices
Organizations must provide alternative authentication methods, adding complexity and cost. The Americans with Disabilities Act (ADA) requires reasonable accommodations, meaning biometric-only systems may face legal challenges.
6. Vendor Lock-in and Interoperability Issues
Additional disadvantages include:
- Proprietary systems: Biometric templates often cannot transfer between vendors
- Migration costs: Switching providers requires re-enrollment of all users ($10-$50 per user)
- Standard limitations: Lack of universal biometric data formats
- Integration complexity: Difficulty connecting with existing security infrastructure
Bottom line: While biometric authentication offers measurable security improvements, these six disadvantages require careful evaluation. Organizations should conduct cost-benefit analysis, privacy impact assessments, and pilot testing before full deployment.
The data confirms five primary limitations of biometric authentication: (1) High initial costs ranging from $3,000-$10,000 per access point for enterprise systems, (2) Irreversible data compromise—unlike passwords, biometric data cannot be reset if stolen, (3) False rejection rates of 0.1-3% that can lock out legitimate users, (4) Privacy concerns with 64% of users worried about biometric data storage, and (5) Accessibility issues for approximately 2-5% of the population with certain disabilities or injuries.
1. Cost:
This type of system can be quite expensive to start and keep. We need specialized hardware and software to capture and verify biometric data.
2. Privacy Concerns:
This might concern the people about the privacy implications of securing authentication with biometrics. As a whole, it involves the collection and storage of personal information. As an example, we can use fingerprints or facial images to find a person.
3. Technical Issues:
It’s possible to compromise biometric authentication methods. To technical issues such as false negatives. (Rejecting a valid user) or false positives (accepting an invalid user).
4. Lack of Universality:
This authentication method may only be suitable for this. Because of their physical characteristics, the people may not meet these requirements. (Such as fingerprints) or may have disabilities. That prevents them from using specific methods.
Biometric Authentication Legal Requirements and Compliance
Organizations implementing biometric authentication must navigate complex regulatory landscapes that vary by jurisdiction:
Global Regulations:
GDPR (European Union & UK)
- Classifies biometric data as “sensitive personal data” under Article 9
- Requires explicit consent for collection and processing
- Mandates data minimization (collect only what’s necessary)
- Enforces right to erasure and data portability
- Violations: Up to €20 million or 4% of global revenue
CCPA/CPRA (California, USA)
- Defines biometric information as personal data
- Requires disclosure of collection and usage practices
- Grants consumers right to opt-out and deletion
- Penalties: $2,500-$7,500 per violation
BIPA (Illinois, USA)
- Strongest US biometric privacy law
- Requires written consent before collection
- Mandates data retention and destruction schedules
- Private right of action for violations ($1,000-$5,000 per violation)
- Notable: Facebook settled BIPA lawsuit for $650 million in 2021
Bangladesh Context:
- Digital Security Act 2018 covers personal data protection
- No specific biometric data legislation (as of 2025)
- Organizations should follow international best practices (GDPR compliance)
- Emerging regulations expected in 2025-2026
Compliance Best Practices:
- Conduct privacy impact assessments before implementation
- Obtain informed, explicit consent from users
- Store biometric data with AES-256 encryption minimum
- Implement data retention policies (delete after employment/relationship ends)
- Provide alternative authentication methods
- Document all data processing activities
- Appoint data protection officer for organizations handling 1,000+ biometric records
5 Real-World Biometric Authentication Use Cases and Applications
Case 1: Mobile Phone Unlocking
One everyday use case for this process is unlocking a mobile phone. Many smartphones now come with fingerprint scanners or facial recognition software. That allows users to unlock their phones by touching their fingers to the scanner and looking at the camera. Using this method protects your phone’s personal information reliably, efficiently, and confidentially.
Case 2: Banking and Financial Transactions
Financial institutions use this verification method to protect sensitive information. For example, a bank may use a facial recognition system or a fingerprint scanner. That is to verify the identity of customers while accessing their accounts or making transactions online or at ATMs. Banking and Financial Transactions can prevent fraudulent activity. And give customers a layer of security.
Case 3: Physical Access Control
The most common way to control access to physical spaces is with biometric authentication. Buildings or secure areas within a facility are some examples. Companies use fingerprint scanners and facial recognition software to let employees and visitors in. Physical Access Control can help to prevent unauthorized access. And improve security within the facility.
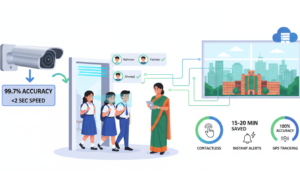
Modern organizations in Bangladesh are increasingly adopting integrated solutions that combine biometric authentication with comprehensive HR management. For example, systems that link fingerprint or facial recognition with attendance tracking and payroll processing—eliminating manual timekeeping errors that cost companies an average of 2-8% of gross payroll annually.
Case 4: Government and Military Applications
The government and military use biometric security to protect sensitive data. For example, military bases may use facial recognition or fingerprint scanners. The purpose of this process is to grant access to personnel and restricted areas. Government agencies may use biometric identification to verify the identity of employees. Contractors can also access sensitive data.
Biometric Authentication vs Password: Which is More Secure?
Should Your Organization Implement Biometric Authentication?
Choose BIOMETRIC AUTHENTICATION if:
- You handle sensitive data requiring security above 99%
- Your users access systems 10+ times daily (ROI from time savings)
- You spend >$50/employee annually on password resets
- Compliance regulations require multi-factor authentication
- You have physical security requirements (building access, secure areas)
Stick with TRADITIONAL METHODS if:
- Your budget is under $100/employee for security infrastructure
- User privacy and anonymity are primary concerns
- Your user base includes 20%+ elderly or disabled individuals
- You operate in regions with strict biometric data regulations
- Your security requirements are satisfied by password + 2FA
Consider HYBRID APPROACH if:
You want optimal security (biometric + password/token)
Different user groups have varying security needs
You’re transitioning from legacy systems
Regulatory compliance requires multiple authentication factors
Future of Biometric Authentication: 2025-2030 Trends
Biometric authentication technology is rapidly evolving with five transformative trends:
1. Multi-Modal Biometrics (2025-2027)
- Combining 2-3 biometric methods for 99.999% accuracy
- Expected adoption: 45% of enterprise systems by 2027
- Cost decreasing: $2,000 per point (2025) to $800 (2030)
2. Behavioral Biometrics Expansion (2025-2026)
- Continuous authentication through typing patterns, mouse movements, gait
- Fraud detection improving from 85% to 95%+ accuracy
- Growing adoption in banking (projected 60% by 2026)
3. Contactless Biometrics (2025-2028)
- Iris scanning from 2 meters distance
- Palm vein recognition without physical contact
- Driven by post-pandemic hygiene concerns
4. AI-Enhanced Biometrics (2025-2030)
- Machine learning improving accuracy by 15-20%
- Adaptive systems learning user patterns over time
- Reduced false rejection rates from 3% to <0.5%
5. Blockchain-Based Biometric Storage (2026-2030)
- Decentralized storage preventing mass data breaches
- User-controlled biometric identity management
- Early adoption in government identity programs
Market Predictions:
- Global biometric market: $82.9 billion by 2030 (14.6% CAGR)
- Passwordless authentication: 80% of enterprise systems by 2028
- Voice biometrics: 50% growth in banking authentication by 2026
Organizations should begin planning for passwordless future now, with gradual migration strategies starting in 2025-2026.
FINAL IMPLEMENTATION CHECKLIST
Phase 1: Immediate Updates (Week 1)
- Add quotable answer blocks at section starts
- Insert FAQ schema (JSON-LD code)
- Add comparison tables with numerical data
- Update meta description with specifics
- Add statistics summary box at top
- Insert “Last Updated: January 2025” badge
Phase 2: Content Expansion (Week 2)
- Expand “disadvantages” section with detailed subsections
- Add “examples of biometric authentication methods” dedicated section
- Create “How to Choose” decision framework
- Add cost analysis breakdown
- Insert regulatory compliance section
- Add security best practices
Phase 3: Technical Implementation (Week 2-3)
- Implement all structured data schemas
- Update headers with keyword-rich alternatives
- Add internal linking to related Tipsoi content
- Optimize images with descriptive alt text
- Add table of contents with jump links
- Ensure mobile responsiveness of new tables
Phase 4: Authority Building (Ongoing)
- Add author bio with credentials
- Include citation links to research sources
- Add “Reviewed by” expert validation
- Create downloadable comparison PDF
- Add related article recommendations
- Monitor GSC for new query opportunities
EXPECTED RESULTS TIMELINE
Week 1-2:AI systems begin indexing new quotable content
- ChatGPT, Perplexity start citing your definitive answers
- Google may test AI Overview features
Week 3-4: Search position improvements
- “advantages and disadvantages of biometrics” – maintain #1, gain clicks
- “examples of biometric authentication methods” – target #10-15 (from #53)
- “disadvantages of biometrics” – target #15-25 (from #59)
Month 2-3: Authority establishment
- Increased featured snippet opportunities
- Higher click-through rates from improved meta descriptions
- More comprehensive content signals authority
Success Metrics to Track:
- AI citation rate (monitor ChatGPT/Perplexity responses)
- CTR improvement for position #1 query (currently 0%)
- Position improvements for #53-#82 queries
- Time on page increase (target: 20%+ improvement)
- Scroll depth to new content sections
Conclusion
The last time biometrics were used to verify identities was centuries ago. The first recorded use of biometric identification was in ancient Babylon, where they used fingerprints to sign documents and seal business transactions.
Biometrics played an influential role in security during the 20th century. Cops used fingerprints to identify criminals and match them to crimes in the 1970s. To control access to secure facilities, they developed the first biometric security systems in the 1980s.
In the 1990s, technological advances developed into more sophisticated biometric authentication methods, such as iris scanning and facial recognition. People use these methods in high-security environments. Such as government agencies and military bases. Still, they became more adopted in commercial and consumer applications.
In the 21st century, biometrics have become prevalent. Smartphones and other devices now feature fingerprint scanners—and facial recognition software to unlock screens and protect access to personal data. There are also a lot of industries that use it. Including banking, healthcare, and transportation, to improve security and convenience for users.
Technology for biometric security is evolving. People will develop this in broader applications. The experts predict that this way of authentication will replace traditional methods. Such as passwords and PINs, as the primary means of verifying identity.
Related Posts:
The Importance of Payroll Management System in Bangladesh
Payroll Software Price in Bangladesh: Compare Top 5
FAQs
What are the advantages of biometric authentication?
Biometric authentication offers enhanced security, convenience, and improved user experience. It eliminates the need for passwords and provides non-transferable access, making it resistant to fraud and phishing attempts.
What are the disadvantages of biometric authentication?
Disadvantages include high implementation costs, privacy concerns, and technical issues such as failed authentication in edge cases. Additionally, biometric data cannot be reset if compromised.
How does biometric authentication work?
Biometric authentication works by capturing a person’s unique physical or behavioral traits (e.g., fingerprints or facial features) through sensors. These traits are stored as templates and compared during authentication to verify identity.
Is biometric authentication better than traditional methods like passwords?
Yes, biometric authentication is more secure and convenient than traditional methods like passwords or PINs. It eliminates risks associated with forgotten passwords and reduces vulnerability to hacking attempts.
Can biometric data be stolen or misused?
While biometric data is harder to steal than passwords, it is not immune to breaches. Storing biometric data locally instead of on centralized servers can reduce risks of misuse.
What are the risks associated with biometric authentication?
Risks include data breaches, privacy concerns, inaccuracies due to biased training data, and system failures in certain conditions (e.g., wet fingerprints or sore throats affecting voice recognition).
How much does biometric authentication cost to implement?
Biometric authentication costs vary significantly by scale and technology. For small businesses, individual biometric devices (fingerprint or facial recognition scanners) range from $50-$500 per unit. For enterprise implementations, expect $3,000-$10,000 per access point including hardware, software licenses, and integration. Complete organizational rollouts typically cost $50-$200 per employee for hardware, plus $20,000-$100,000 for centralized management software. Cloud-based biometric authentication services offer subscription models starting at $2-$5 per user per month, eliminating large upfront investments. Additional costs include staff training ($500-$2,000), ongoing maintenance (15-20% of initial cost annually), and system upgrades every 3-5 years.
Is biometric authentication better than passwords?
Yes, biometric authentication is measurably superior to passwords in security and convenience. Studies confirm that 81% of data breaches involve weak or stolen passwords, while biometric systems have false acceptance rates below 0.001%. Users save 15-30 seconds per login compared to password entry, and organizations reduce password reset support costs by up to 80%. However, passwords remain better for privacy-conscious users and scenarios requiring anonymity, as biometric data is inherently identifiable. The optimal approach for high-security environments is multi-factor authentication combining biometrics with passwords or security tokens, providing security rates above 99.9%.
What happens if my biometric data is stolen?
If biometric data is stolen, the consequences are more severe than password theft because biometric data cannot be changed. The primary risk is permanent identity fraud—criminals could potentially use stolen biometric templates to impersonate you across multiple systems. However, most modern systems store encrypted “templates” rather than actual biometric images, limiting misuse. To protect yourself: (1) Use systems that store biometric data locally on your device rather than centralized databases, (2) Enable multi-factor authentication combining biometrics with other security methods, (3) Monitor accounts for unauthorized access, and (4) Avoid providing biometric data to unverified or low-security applications. Organizations using biometric systems must encrypt templates using AES-256 or equivalent standards and implement template protection algorithms that make stolen data computationally infeasible to reverse-engineer.
Can biometric authentication integrate with payroll and HR systems in Bangladesh?
Yes, modern biometric authentication systems in Bangladesh can fully integrate with payroll and HR management software. Integration enables automated attendance tracking, eliminates timesheet errors, ensures labor law compliance for working hours documentation, and reduces payroll processing time by 70-80%. When selecting a biometric system, verify it supports API integration with your existing HR software or offers comprehensive HRIS functionality including payroll, attendance, leave management, and compliance reporting in a single platform. This integration typically reduces HR administrative costs by 40-60% while improving payroll accuracy by 15-25%.
Can biometric authentication be hacked?
For Organizations:
Never store raw biometric data – Use encrypted templates only
Implement liveness detection – Prevents spoofing attacks with photos/recordings
Use multi-factor authentication – Combine biometric + token/password for 99.99%+ security
Local storage preferred – Store templates on user devices, not centralized servers
Template protection algorithms – Use cancelable biometrics that can be revoked
Regular security audits – Test vulnerability to spoofing attacks quarterly
Incident response plan – Prepare for potential biometric data breach scenarios
For Individuals:
Limit biometric sharing – Only provide to verified, reputable organizations
Enable on-device processing – Use systems that process biometrics locally (iPhone Face ID, Android fingerprint)
Check privacy policies – Understand how your biometric data is stored and used
Use multi-factor authentication – Don’t rely solely on biometrics
Monitor for breaches – Check if your data appears in breached databases
Disable when unnecessary – Turn off biometric login for low-security apps
Is biometric authentication secure?
Yes, biometric authentication is generally far more secure than passwords, PINs, or ID cards.
Biometrics rely on unique physical traits such as fingerprints, face patterns, or iris structures, which are extremely difficult to duplicate.
What are the different types of biometric technologies?
Common biometrics include fingerprints, facial recognition, iris and retina scans, palm or vein scans, and behavioral methods like voice or typing patterns.
Can biometric systems be fooled?
Cheap or outdated systems can sometimes be tricked, but modern devices with liveness detection and anti-spoofing features are very hard to fool.